Phishing involves deceptive emails or websites to steal personal information, while skimming uses physical devices to capture credit card details during transactions. Discover more about how to protect yourself from these cyber threats in this article.
Table of Comparison
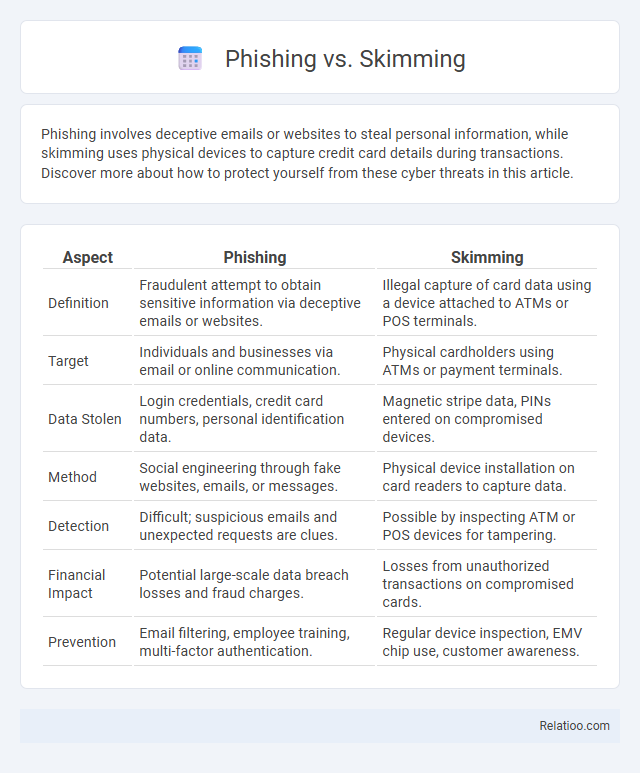
| Aspect | Phishing | Skimming |
|---|---|---|
| Definition | Fraudulent attempt to obtain sensitive information via deceptive emails or websites. | Illegal capture of card data using a device attached to ATMs or POS terminals. |
| Target | Individuals and businesses via email or online communication. | Physical cardholders using ATMs or payment terminals. |
| Data Stolen | Login credentials, credit card numbers, personal identification data. | Magnetic stripe data, PINs entered on compromised devices. |
| Method | Social engineering through fake websites, emails, or messages. | Physical device installation on card readers to capture data. |
| Detection | Difficult; suspicious emails and unexpected requests are clues. | Possible by inspecting ATM or POS devices for tampering. |
| Financial Impact | Potential large-scale data breach losses and fraud charges. | Losses from unauthorized transactions on compromised cards. |
| Prevention | Email filtering, employee training, multi-factor authentication. | Regular device inspection, EMV chip use, customer awareness. |
Introduction to Phishing and Skimming
Phishing involves fraudulent attempts to obtain sensitive information by disguising as trustworthy entities through emails or websites. Skimming refers to the illegal copying of credit or debit card data using a small device installed on card readers. Understanding these scams helps protect Your personal and financial information from being exploited by cybercriminals.
Defining Phishing: How It Works
Phishing is a cyberattack method where attackers impersonate legitimate entities to trick individuals into revealing sensitive information such as passwords, credit card numbers, or Social Security details through fraudulent emails or websites. It leverages social engineering techniques, creating a sense of urgency or trust to deceive victims into voluntarily providing personal data. Phishing differs from skimming, which involves physical card data theft via electronic devices, and identity theft, which broadly encompasses unauthorized use of personal information to commit fraud.
Understanding Skimming: An Overview
Skimming involves the illegal capture of credit or debit card information using a small device placed on card readers, often at ATMs or point-of-sale terminals. This stolen data allows criminals to create counterfeit cards or make unauthorized transactions, severely impacting your financial security. Understanding the mechanics of skimming can help you recognize suspicious devices and protect your personal information from theft.
Techniques Used in Phishing Attacks
Phishing attacks primarily employ deceptive techniques such as email spoofing, malicious links, and fake websites to trick users into revealing sensitive information like passwords and credit card numbers. Attackers often use social engineering tactics to create a sense of urgency or trust, increasing the likelihood of victim compliance. These sophisticated methods distinguish phishing from skimming, which involves physical theft of card data, and identity theft, which broadly encompasses unauthorized use of personal information for fraudulent purposes.
Common Methods of Skimming
Skimming commonly involves the use of small devices called skimmers placed on ATMs, gas station pumps, or point-of-sale terminals to illegally capture card information during legitimate transactions. Thieves often employ tiny cameras or fake keypads to record PIN entries alongside stolen card data. This method differs from phishing, which targets personal information through deceptive online communications, and identity theft, which uses stolen data to impersonate victims for financial fraud.
Key Differences Between Phishing and Skimming
Phishing involves deceptive emails or websites designed to trick users into revealing sensitive information, such as passwords or credit card numbers, while skimming refers to the physical or electronic theft of card data using devices installed on ATMs or point-of-sale terminals. Phishing attacks exploit social engineering and digital communication channels, whereas skimming relies on hardware to capture data during legitimate transactions. Understanding these key differences is crucial for implementing targeted cybersecurity measures against identity theft and financial fraud.
Real-World Examples of Phishing Scams
Phishing scams often involve fraudulent emails or fake websites designed to steal login credentials, as seen in the 2016 Democratic National Committee email breach. Skimming involves criminals installing devices on ATMs or gas pumps to capture card information covertly, exemplified by the 2018 British Airways data skimming attack. Identity theft frequently results from these methods, where stolen personal information is used to open fraudulent accounts or make unauthorized purchases, as in the widespread Equifax breach of 2017 affecting millions.
Notable Skimming Incidents and Cases
Notable skimming incidents include the 2013 ATM skimming operation in the United States, where criminals installed sophisticated card readers and cameras to capture card data and PINs, resulting in millions of dollars in fraudulent transactions. Another significant case is the 2018 global skimming ring that targeted gas station pumps across Europe, compromising thousands of customers' payment information. These skimming attacks differ from phishing and identity theft in their direct physical capture of card data rather than tricking individuals through communication or broader personal data breaches.
Preventive Measures Against Phishing
Phishing attacks exploit deceptive emails or websites to steal your sensitive information, often masquerading as legitimate entities. Skimming involves capturing card data through physical devices on ATMs or point-of-sale terminals, while identity theft steals your personal data for fraudulent purposes. Implement strong email filters, verify website URLs before entering credentials, and use multi-factor authentication to effectively prevent phishing threats.
How to Protect Yourself from Skimming
Skimming involves the illegal capture of your credit or debit card information through devices placed on legitimate payment terminals. Protect your financial data by regularly inspecting ATMs and point-of-sale machines for unusual attachments, covering the keypad when entering your PIN, and using contactless payment options when possible. Staying vigilant and promptly reviewing your bank statements can help you detect unauthorized transactions early and safeguard your identity.
Infographic: Phishing vs Skimming
 relatioo.com
relatioo.com