Vulnerability in relationships refers to the emotional openness that fosters deep connection, while exposure involves risk without trust, often leading to discomfort. Discover how balancing vulnerability and exposure can strengthen your bonds in this article.
Table of Comparison
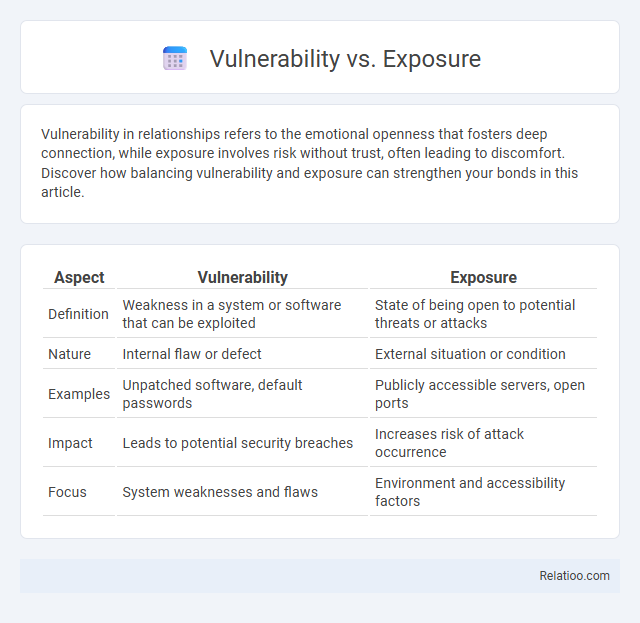
| Aspect | Vulnerability | Exposure |
|---|---|---|
| Definition | Weakness in a system or software that can be exploited | State of being open to potential threats or attacks |
| Nature | Internal flaw or defect | External situation or condition |
| Examples | Unpatched software, default passwords | Publicly accessible servers, open ports |
| Impact | Leads to potential security breaches | Increases risk of attack occurrence |
| Focus | System weaknesses and flaws | Environment and accessibility factors |
Understanding Vulnerability and Exposure
Vulnerability refers to the inherent weaknesses or flaws within a system that can be exploited by threats, while exposure measures the extent to which these vulnerabilities are accessible to potential attackers. Understanding vulnerability and exposure is crucial for effective risk management, as it enables organizations to identify critical points that require protection and prioritize security efforts accordingly. Harmonizing these concepts ensures a balanced approach to defense, reducing the likelihood of successful breaches by addressing both system weaknesses and their accessibility.
Key Differences Between Vulnerability and Exposure
Vulnerability refers to inherent weaknesses in a system or asset that can be exploited by threats, whereas exposure indicates the extent to which your system is susceptible to potential threats based on its configuration or environment. Vulnerabilities are specific flaws requiring mitigation, while exposure defines the conditions that make these vulnerabilities accessible to attackers. Understanding these key differences helps in harmonizing security strategies by prioritizing both patching vulnerabilities and reducing exposure risks.
The Role of Vulnerability in Risk Assessment
Vulnerability represents the inherent weaknesses within your systems or processes that attackers can exploit, directly increasing your risk exposure and potential impact. Exposure refers to the extent to which your assets are accessible or susceptible to threats, while harmonizing involves aligning security measures and risk management strategies to address vulnerabilities effectively. Understanding the role of vulnerability in risk assessment enables you to prioritize mitigations and reduce the likelihood and severity of security incidents.
How Exposure Impacts Security Posture
Exposure directly influences Your security posture by increasing the likelihood that vulnerabilities will be exploited by threat actors, turning potential weaknesses into active risks. Vulnerability represents inherent weaknesses in systems, but without exposure, these vulnerabilities remain dormant and less dangerous. Harmonizing security measures involves reducing exposure by strengthening defenses and minimizing attack surfaces, thereby enhancing overall resilience against cyber threats.
Real-World Examples: Vulnerability vs Exposure
Understanding the difference between vulnerability and exposure is crucial in cybersecurity, as vulnerability refers to weaknesses in your system that attackers can exploit, while exposure denotes the degree to which these vulnerabilities are accessible or visible to potential threats. For example, an outdated software with known security flaws represents a vulnerability, but if it resides within an isolated network without internet access, your exposure is low. Your security posture improves significantly when you identify vulnerabilities and limit their exposure through robust access controls and network segmentation.
Identifying Vulnerabilities in Your Systems
Identifying vulnerabilities in your systems requires a thorough assessment of potential weaknesses that could be exploited by threats, distinguishing these from mere exposures that represent potential entry points without immediate risk. Vulnerability scanning tools and penetration testing methodologies help uncover security gaps, enabling prioritization based on severity and exploitability. Harmonizing these findings with exposure data ensures a comprehensive risk management strategy, enhancing your system's resilience and reducing the attack surface effectively.
Assessing Exposure in Modern IT Environments
Assessing exposure in modern IT environments requires identifying vulnerabilities within software, hardware, and network configurations that could be exploited by attackers. Exposure quantifies the potential points of unauthorized access or data leakage across cloud services, IoT devices, and on-premises systems. You must implement continuous monitoring and risk assessment tools to harmonize vulnerability management with real-time exposure insights, ensuring robust security posture against evolving threats.
Mitigation Strategies for Vulnerabilities and Exposures
Effective mitigation strategies for vulnerabilities and exposures involve a comprehensive approach combining timely patch management, continuous monitoring, and risk assessment frameworks tailored to specific threat landscapes. Implementing automated scanning tools alongside manual penetration testing enhances the identification and prioritization of security gaps, enabling targeted application of controls. Harmonizing these measures with organizational policies and compliance requirements optimizes resilience against exploitable weaknesses and minimizes potential attack surfaces.
Tools for Detecting and Managing Vulnerability and Exposure
Tools for detecting and managing vulnerability and exposure include advanced vulnerability scanners, penetration testing software, and real-time exposure monitoring platforms. These tools identify weaknesses in systems, assess potential attack vectors, and provide actionable insights to prioritize risk mitigation. Harmonizing these tools through integrated security frameworks enhances comprehensive risk assessment and streamlines remediation workflows for sustained protection.
Best Practices for Reducing Risk
Understanding vulnerability involves identifying weaknesses in your systems that attackers can exploit, while exposure refers to the extent these vulnerabilities are accessible to threats. Harmonizing security measures means integrating risk management strategies to address both vulnerabilities and exposure effectively. You can reduce risk by continuously updating patches, implementing robust access controls, and conducting regular security assessments to align your defenses with evolving threats.
Infographic: Vulnerability vs Exposure
 relatioo.com
relatioo.com