Vulnerability in relationships refers to openness and emotional honesty, fostering deeper connection and trust, while threats undermine this safety by introducing fear or harm. Explore this article to understand how balancing vulnerability and recognizing threats can strengthen your bonds.
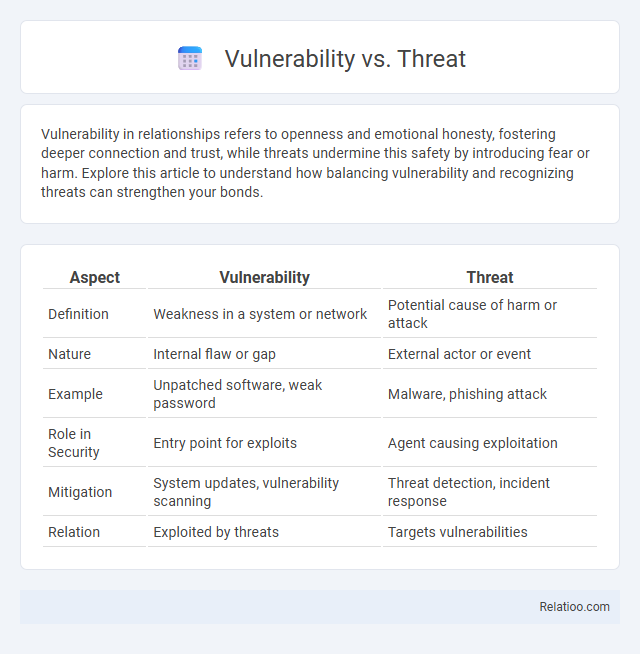
Table of Comparison
| Aspect | Vulnerability | Threat |
|---|---|---|
| Definition | Weakness in a system or network | Potential cause of harm or attack |
| Nature | Internal flaw or gap | External actor or event |
| Example | Unpatched software, weak password | Malware, phishing attack |
| Role in Security | Entry point for exploits | Agent causing exploitation |
| Mitigation | System updates, vulnerability scanning | Threat detection, incident response |
| Relation | Exploited by threats | Targets vulnerabilities |
Understanding Vulnerability and Threat: Core Definitions
Vulnerability refers to weaknesses or gaps in a system that can be exploited by threats, which are potential sources of harm targeting these vulnerabilities. Understanding the distinction between vulnerability and threat is essential for accurately assessing risk and implementing effective security measures. Harmonizing these concepts involves aligning vulnerability management with threat intelligence to create a robust defense strategy.
Key Differences Between Vulnerability and Threat
Vulnerability refers to weaknesses or flaws within a system, network, or application that can be exploited, while a threat is any potential danger or malicious actor capable of exploiting those vulnerabilities to cause harm. Understanding the key differences between vulnerability and threat helps you prioritize risk management strategies and allocate resources effectively. Harmonizing these concepts involves integrating vulnerability assessments and threat intelligence to create a robust security posture.
Types of Vulnerabilities in Cybersecurity
Vulnerabilities in cybersecurity include software bugs, misconfigurations, and weak authentication mechanisms that attackers exploit to compromise systems. Threats represent potential malicious actions or events targeting these vulnerabilities, such as malware, phishing, or insider attacks. Harmonizing your security involves integrating threat intelligence with vulnerability management to prioritize risk and reinforce defenses effectively.
Common Threats Facing Organizations Today
Common threats facing organizations today include ransomware attacks, phishing scams, insider threats, and supply chain vulnerabilities. Your ability to identify vulnerabilities within your systems is crucial for mitigating these risks and strengthening cybersecurity defenses. Harmonizing security policies and threat intelligence enables a cohesive strategy that reduces exposure to evolving cyber threats.
How Vulnerabilities Lead to Threat Exposure
Vulnerabilities are weaknesses in your systems, software, or processes that can be exploited by threats, increasing the risk of unauthorized access, data breaches, or service disruptions. When these vulnerabilities remain unaddressed, they create entry points for cyberattacks, escalating your exposure to various threats such as malware, phishing, or insider attacks. Harmonizing security measures by identifying, prioritizing, and mitigating vulnerabilities effectively reduces threat exposure and strengthens your overall cybersecurity posture.
Assessing and Identifying Vulnerabilities
Assessing and identifying vulnerabilities involves systematically examining your systems, networks, and applications to uncover weaknesses that could be exploited by threats. Vulnerabilities represent potential security gaps, while threats are the external or internal actors that may leverage these weaknesses to cause harm. Harmonizing vulnerability assessments with threat intelligence enables you to prioritize risks effectively and strengthen your overall security posture.
Evaluating and Prioritizing Threats
Evaluating and prioritizing threats involves assessing system vulnerabilities to identify potential security weaknesses that adversaries can exploit. Threat evaluation considers the likelihood and impact of various attack vectors, enabling organizations to rank threats based on severity and potential damage. Harmonizing this process integrates vulnerability assessments with threat intelligence, improving the precision in allocating resources to mitigate high-priority risks effectively.
Risk Management: Addressing Vulnerabilities and Threats
Vulnerability refers to weaknesses in systems or processes that expose organizations to potential harm, while threats are external factors or actors seeking to exploit these vulnerabilities. Effective risk management requires identifying and prioritizing vulnerabilities and threats to develop targeted strategies that minimize potential impact. Harmonizing risk management integrates assessment, mitigation, and continuous monitoring to ensure comprehensive protection against evolving cybersecurity challenges.
Best Practices for Mitigating Vulnerabilities and Threats
Effective mitigation of vulnerabilities and threats requires a comprehensive approach integrating continuous vulnerability assessment, threat intelligence, and proactive remediation strategies. Regularly updating software, applying security patches, and implementing multi-layered defense mechanisms reduce attack surfaces and minimize the risk of exploitation. Harmonizing security policies across the organization enhances incident response efficiency and ensures consistent application of best practices.
Future Trends in Vulnerability and Threat Management
Future trends in vulnerability and threat management emphasize the integration of AI-powered predictive analytics to identify emerging cybersecurity risks and streamline response strategies. Innovations in harmonizing vulnerability data across diverse platforms enhance real-time threat intelligence sharing, reducing response time to cyberattacks. The evolution of adaptive security frameworks supports proactive risk mitigation by continuously aligning vulnerability assessments with dynamic threat landscapes.
Infographic: Vulnerability vs Threat
 relatioo.com
relatioo.com