Snoop relationships involve passive observation without interference, while intrusive relationships are characterized by invasive and controlling behaviors. Discover more about managing these dynamics effectively in this article.
Table of Comparison
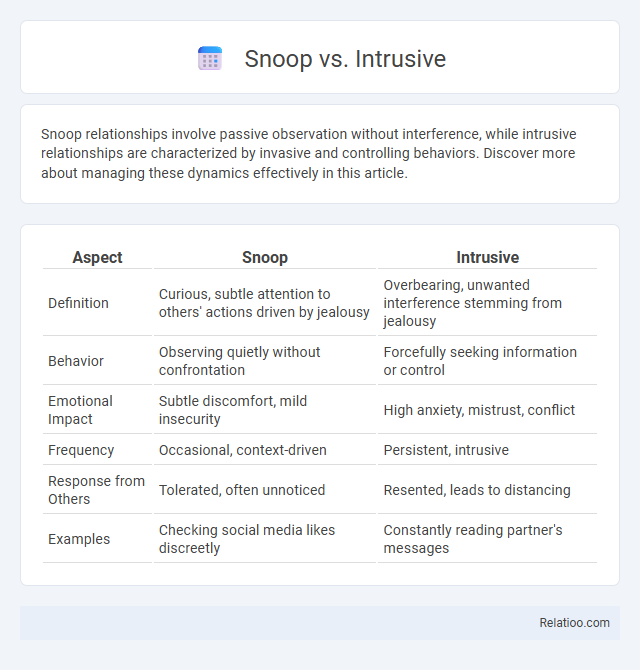
| Aspect | Snoop | Intrusive |
|---|---|---|
| Definition | Curious, subtle attention to others' actions driven by jealousy | Overbearing, unwanted interference stemming from jealousy |
| Behavior | Observing quietly without confrontation | Forcefully seeking information or control |
| Emotional Impact | Subtle discomfort, mild insecurity | High anxiety, mistrust, conflict |
| Frequency | Occasional, context-driven | Persistent, intrusive |
| Response from Others | Tolerated, often unnoticed | Resented, leads to distancing |
| Examples | Checking social media likes discreetly | Constantly reading partner's messages |
Understanding Snoop vs Intrusive: Key Differences
Snoop and Intrusive cache coherence protocols differ primarily in how they monitor and maintain consistency across multiple processors' caches. Snoop protocols rely on broadcasting cache state information to all processors, enabling each to track sharing status without direct permission checks, while Intrusive protocols actively intercept and modify cache lines, enforcing coherence by controlling access permissions. Understanding these mechanisms is crucial for optimizing multicore processor performance and memory consistency models.
The Psychology Behind Snooping and Intrusiveness
The psychology behind snooping and intrusiveness reveals underlying issues of trust, control, and insecurity within relationships. Individuals who engage in snooping often seek reassurance or hidden truths, driven by anxiety or fear of betrayal. This behavior blurs boundaries and can escalate from simple curiosity to intrusive actions that damage communication and emotional intimacy.
Common Scenarios: Snoop vs Intrusive Behavior
Snoop behavior involves discreetly observing others' actions or conversations without their knowledge, often driven by curiosity or suspicion, while intrusive behavior crosses boundaries by actively interfering or invading personal spaces. Common scenarios of snoop vs intrusive behavior include checking a partner's phone (snoop) versus reading their private messages aloud to others (intrusive). Your awareness of these distinctions helps maintain respectful interactions and protect personal privacy effectively.
Recognizing Boundaries: When Curiosity Turns Intrusive
Recognizing boundaries is crucial when distinguishing between harmless snooping and intrusive behavior. Your curiosity can become problematic if it invades privacy, causing discomfort or harm. Understanding when to respect personal limits ensures interactions remain respectful and considerate.
Social and Ethical Implications of Snooping
Snoop tests involve monitoring user activity to gather data without explicit consent, raising significant social concerns regarding privacy infringement and trust erosion in digital environments. Intrusive snooping exacerbates ethical dilemmas by covertly accessing sensitive information, often violating personal boundaries and legal standards. Balancing these practices requires stringent regulations and transparent policies to protect user rights while addressing legitimate security needs.
Privacy in Relationships: Snoop vs Intrusive Actions
Snoop in relationships involves discreetly seeking information with less obvious intent, while intrusive actions breach privacy by openly monitoring or accessing personal communications without consent. Privacy is compromised more severely through intrusive behaviors, which can erode trust and foster resentment. Understanding the boundaries between curiosity and violation is essential to maintaining healthy, respectful partnerships.
Preventing Intrusiveness: Building Healthy Trust
Snoop technologies focus on monitoring user activities, while intrusive approaches breach personal boundaries, causing distrust and discomfort. Preventing intrusiveness involves implementing transparent data practices and user consent mechanisms that respect privacy and build healthy trust. Your confidence relies on balancing effective surveillance with ethical boundaries to maintain a secure yet respectful environment.
Legal Perspectives: Snoop vs Intrusive Conduct
Legal perspectives on Snoop versus intrusive conduct emphasize the boundaries of privacy rights under laws such as the Fourth Amendment and data protection regulations. Your rights are typically protected against unauthorized snooping when it involves unlawful surveillance, hacking, or accessing personal data without consent. Courts differentiate between lawful monitoring, such as with warrants, and intrusive snooping, which may result in legal penalties for violating privacy laws.
Coping Strategies for Victims of Intrusive Behavior
Victims of intrusive behavior can adopt effective coping strategies such as setting clear personal boundaries and communicating assertively to protect their privacy. Utilizing mindfulness and stress-reduction techniques helps manage anxiety caused by unwanted snooping or surveillance. You can also seek support from trusted friends, family, or professionals to reinforce your emotional resilience and develop practical responses to intrusive situations.
Promoting Respect for Privacy in the Digital Age
Snoop, Intrusive, and Snoop represent varying degrees of data surveillance, where intrusive methods often violate personal boundaries and erode digital trust. Promoting respect for privacy in the digital age requires implementing transparent data practices and empowering users to control their information. Your awareness of these distinctions helps safeguard your digital footprint against unauthorized monitoring.
Infographic: Snoop vs Intrusive
 relatioo.com
relatioo.com